TÜV SÜD uses Honeynet to test how vulnerable small infrastructures are exposed to hacker attacks and reveals a high risk potential.
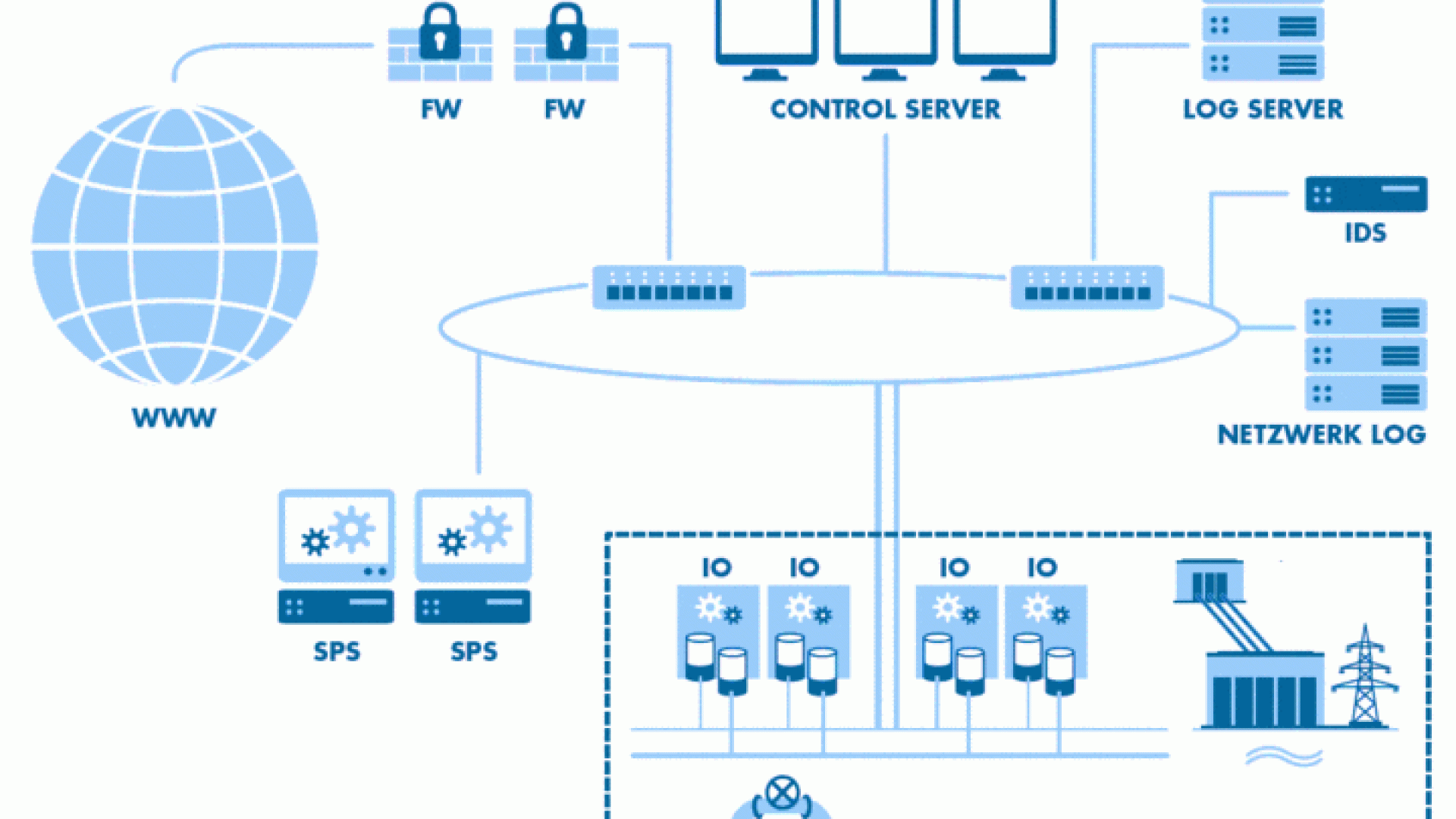
Smaller infrastructures are not interesting for hackers. With this belief, many public utilities and municipalities are convinced that they are safe. This is false. In a Honeynet project, TÜV SÜD has demonstrated that even small infrastructures in the network are being exploited and attacked.
“A Honeynet is a system designed to attract attackers and thus enable precise analysis of access and attack activities”, says Dr Armin Pfoh, Vice President Innovation Management at TÜV SÜD. In the project, TÜV SÜD’s high-interaction Honeynet combined real hardware and software with the simulated environment of a smaller waterworks. During the eight-month project, more than 60,000 hits from 150 countries were recorded. “This demonstrated that even a relatively insignificant infrastructure in the network is observed and tracked down”, explains Dr Thomas Störtkuhl, Team Leader Industrial ITSecurity at TÜV SÜD. Some of the accesses took place via covert or disguised IP addresses.
Particularly, the recognition that access was not only via standard office IT protocols, but also via industrial protocols such as Modbus TCP or S7COMM, is of considerable importance for the operators of supply infrastructures. According to Dr. Störtkuhl, it is, therefore, clear that gaps in the security architecture of control systems can be detected and that even vulnerable small systems are possible targets of hackers.
HST Systemtechnik GmbH & Co. KG
Heinrichsthaler Straße 8
D-59872 Meschede
Tel. +49 - (0) 291-9929-0
Fax. +49 - (0) 291-7691
info@hst.de
Systems without up-to-date protection become extremely vulnerable
The results of the TÜV SÜD project are a clear warning signal. “Even small and supposedly insignificant infrastructures are being spotted because spying activities are constantly happening on the Internet”, stresses Dr Störtkuhl. Operators can thus become the victims of a wave of attacks, even if they have not been specifically targeted. If potential attackers already have an infrastructure on their sights, this makes a targeted attack at a later date all the easier.
Such attacks can cause tremendous damage – from spying on information to sabotaging an entire infrastructure.
“Our Honeynet project shows that many utility infrastructure operators are deceptively secure,” warns Dr. Armin Pfoh. “They expose themselves to high risk if they do not adapt their protection measures.”
Essential components of these measures are focused monitoring and the introduction of an Information Security Management System (ISMS) according to a recognized standard such as ISO/IEC 27001.
Author:
Dr. Thomas Störtkuhl & Dr. Armin Pfoh,
TÜV SÜD Rail GmbH, Munich





